OnePlus announces bug bounty program
Finally, OnePlus has announced that they'll partner up with the security platform HackerOne. With this platform, they also opened a bug bounty program, which means you may get paid for finding vulnerabilities in their system.
This move of OnePlus was expected to happen by the community and other organisations, as OnePlus tends to struggle sometimes in the security-field. With this new program that has just been introduced by OnePlus, we may hopefully see that OnePlus' security platform will be improved.
Who is this meant for?
OnePlus is looking for security researchers of all backgrounds and levels to join OnePlus in their program, in order to find vulnerabilities in the OnePlus ecosystem. For example, if you found a way to misuse a vulnerability and it's eligible for their program, you may get paid up to 7000 dollars (in special cases). For more details, check below.
Rules, eligible issues and rewards
So, the question is: when are you eligible to get a reward? You don't want to spend time on finding a vulnerability, submit your vulnerability and then hear from OnePlus that vulnerability X is not included in their program. Fortunately, OnePlus has stated what they allow and what they don't.
Eligible issues:
- OnePlus official website
- OnePlus Store
- OxygenOS
- OnePlus App Store
- OnePlus Cloud
- OnePlus Community
- OnePlus Account
Exclusions (which means the following things don't count as a vulnerability):
- Denial of service (for example: flooding their servers, backbone and network with an overload of internet traffic doesn't count as a vulnerability. This is probably because it's quite hard to avoid this, unless you take serious steps.
- Spamming (for example: spamming them with emails. Spamfilters don't block all potential harmful email-traffic for example)
- Social engineering (including phishing) of OnePlus staff or contractors (for example: trying to convince employee X to give them their password, by, for example, sending a fake email asking to let an employee fill in their password on a fake website).
- Any physical attempts against OnePlus property or data centers (for example: plugging in an USB-stick, which contains malware into a physical server. This obviously doesn't count as vulnerability).
- Login/logout CSRF (Cross-Site Request Forgery)
- Host header injections without a specific, demonstrable impact
- SPF / DMARC in non-email domains/subdomains
- Error information disclosure that cannot be used to make a direct attack
- Missing security-related HTTP headers which do not lead directly to a vulnerability (for example, see here: https://en.wikipedia.org/wiki/HTTP_header_injection and here: https://en.wikipedia.org/wiki/HTTP_response_splitting
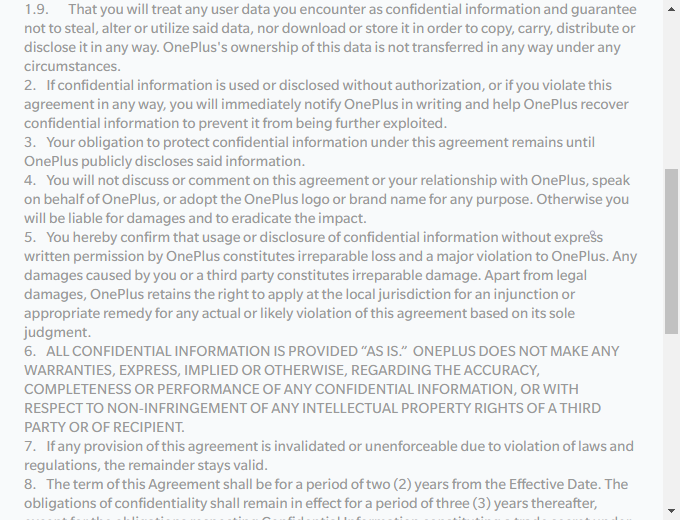
OnePlus' security testing non-disclosure agreement:


Rewards
OnePlus will pay you based on how severe a vulnerability is. For example, a vulnerability which is very easy to misuse and doesn't require a lot of skills will have a higher reward than a vulnerability that is very hard to execute, and which probably involves multiple vulnerabilities to misuse. From high to low:
- Special cases: up to $7,000
- Critical: $750 - $1,500
- High: $250 - $750
- Medium: $100 - $250
- Low: $50 - $100
OnePlus will decide whether it is a low, medium, high, critical, special case or not, probably based on how easy the the vulnerability can be used.
Testing environment vulnerabilities are counted as 0.1 times with OnePlus their OnePlus-owned component counterpart and OnePlus does not accept reports that have been uploaded elsewhere.
Privacy-related note: A bank account number is required for transfer of funds/rewards.
So... how to submit the vulnerability I found?
Earlier, before OnePlus introduced this program, you could send an email to [email protected] to report/submit vulnerabilities. Now, you can simply go to https://security.oneplus.com/add.html, login with your account and fill in the details.
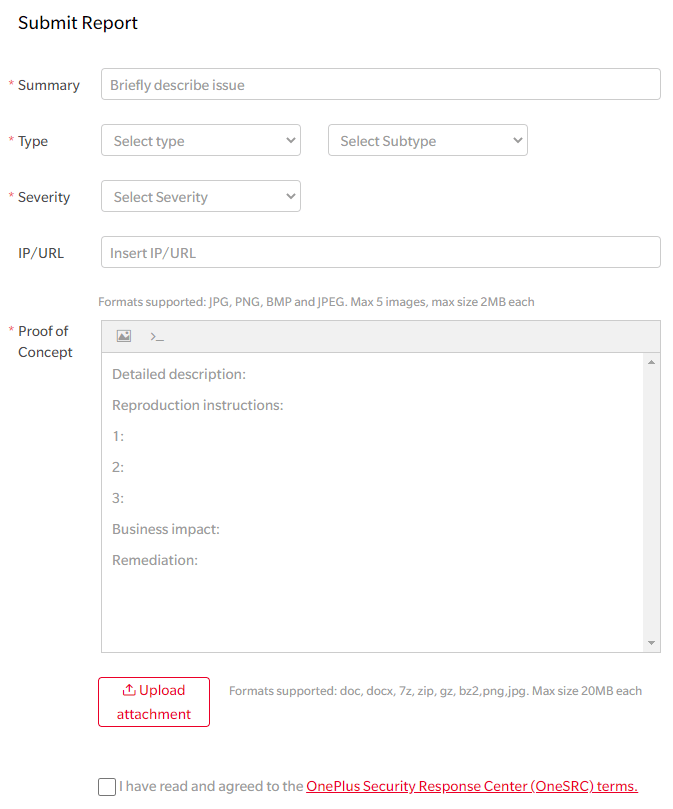
You can find more information down below:
- https://security.oneplus.com/index.html
- https://security.oneplus.com/noticedetails.html?noticeId=20191565338585128
- https://hackerone.com/oneplus
A public version of the program is slated to go live later in 2020.